n8n Users Urged to Patch CVSS 10.0 Full System Takeover Vulnerability https://hackread.com/n8n-users-patch-full-system-takeover-vulnerability/ #ApplicationSecurity #Cybersecurity #Vulnerability #Security #database #Upwind #n8n
Clemens
boosted
n8n Users Urged to Patch CVSS 10.0 Full System Takeover Vulnerability https://hackread.com/n8n-users-patch-full-system-takeover-vulnerability/ #ApplicationSecurity #Cybersecurity #Vulnerability #Security #database #Upwind #n8n
C_ristina
boosted
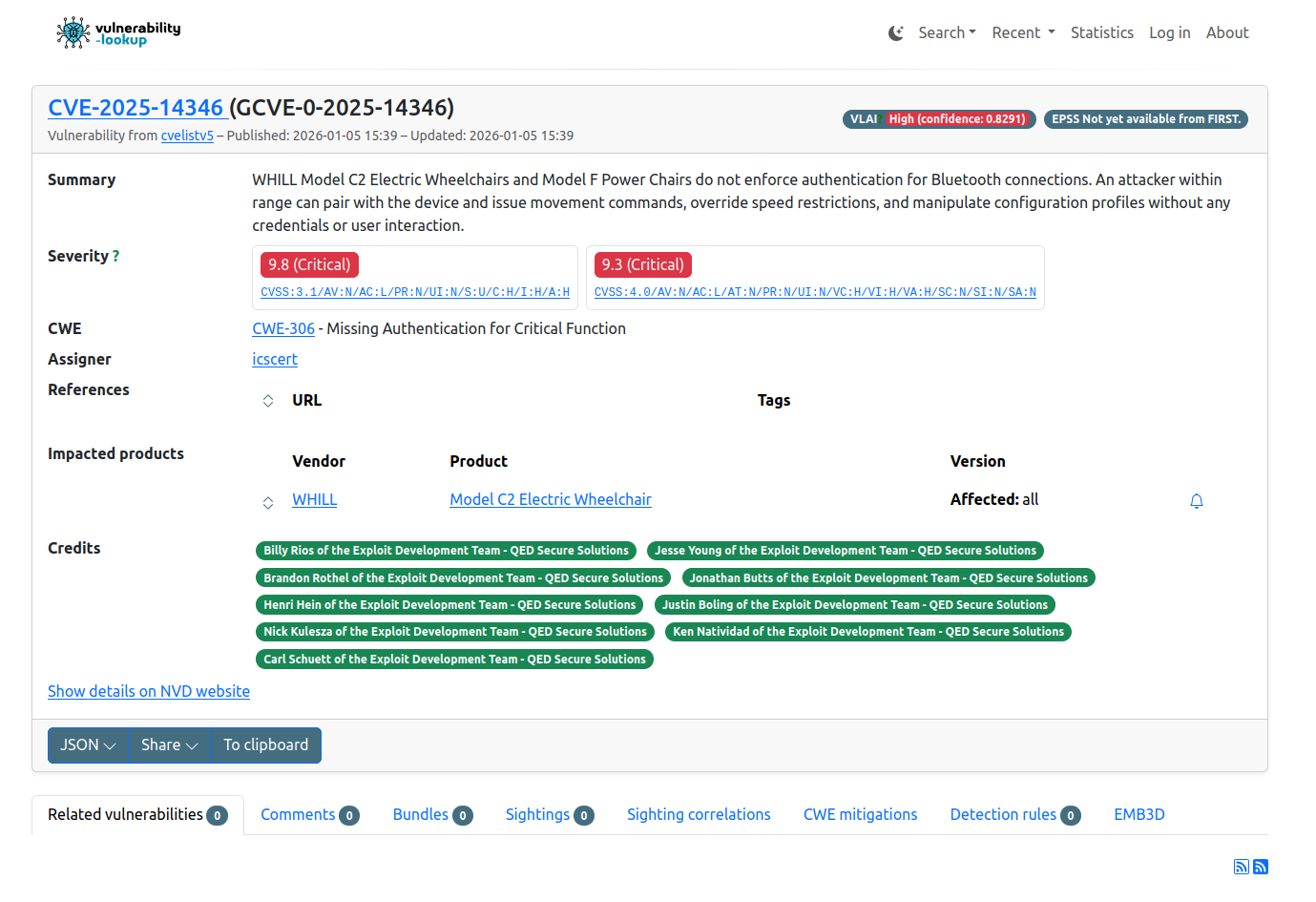
"WHILL Model C2 Electric Wheelchairs and Model F Power Chairs do not enforce authentication for Bluetooth connections. An attacker within range can pair with the device and issue movement commands, override speed restrictions, and manipulate configuration profiles without any credentials or user interaction."
No comments...
1